What Does Cybercrime Look Like?
Have you gone phishing lately? It’s beginning to look a lot like cybercrime is just around the corner. But what does cybercrime look like? And, how will you know if cybercrime will impact your business?
Will my business be impacted by cybercrime?
The short answer is, “It is a question of when–not if.” This should encourage us all to learn a bit more about what the most recent cybercrimes look like and the impact they are making on small businesses.
The types of cybercrime that could potentially impact a business include phishing scams, malware attacks, ransomware attacks, and data breaches. These types of attacks can result in significant financial losses, as well as damage to a company’s reputation.
In this article, we will discuss the importance of cybersecurity insurance for small to mid-sized businesses (SMBs) and why every business should consider it.
What is the most common type of cybercrime today?
- You receive an event email titled “Your Market Growth Strategy Webinar Is About To Start!” but don’t see this event on your calendar or recall registering.
- You receive a voicemail message attachment via email through a notable telecom company, but your company doesn’t utilize its services.
- You receive an email marked “high priority” from what appears to be your boss. He claims to be busy in a meeting and requires urgent action on your part to call a specific number.
These are examples of the leading type of cybercrime today, Phishing. Phishing is the term given to emails that seem legitimate and often create a false sense of urgency, leading you or your employees to click on a malicious link within the message or give away confidential organizational or personal information that can be used to infiltrate your company’s networks.
Phishing emails are typically designed to look like they are from a legitimate source, such as a bank or a reputable company. They often use social engineering techniques to create a sense of urgency or fear, in order to convince the recipient to take the desired action. Phishing emails often ask for personal information, such as login credentials, social security numbers, or credit card numbers. They may also ask the recipient to click on a link or open an attachment, which can be used to install malware or redirect the recipient to a fake website.
Phishing emails can be difficult to detect, as they are often designed to look like legitimate communications from a trusted source. The malicious actors sending phishing emails are depending on finding the right combination of urgency / persuasion and momentary lapse in caution. While you and all of your employees have to be vigilant always, the scammers only have to be lucky once to be successful in causing potentially irreparable damage to your business’ reputation, finances, and operations.
Statistics from Security Boulevard show that in 2020, nearly 1 in 4 of all data breaches involved a phishing attack. Furthermore, 97% of users could not spot a sophisticated phishing email, and 78% of users understood the risk of hyperlinks in emails but clicked on them anyway.
#1 email and Internet fraud: phishing
This Phishing Email Example is what fraud looks like and it’s a good one because it comes from someone you know! Teresa’s email is hacked and now her entire email contact network is receiving this plea for money.
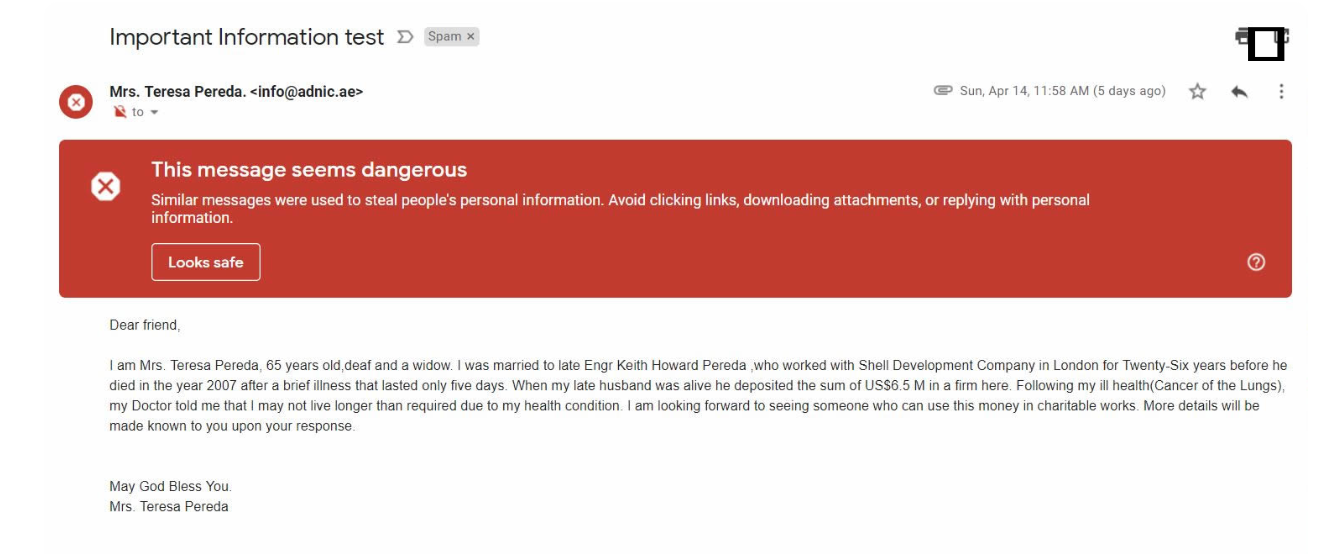
Scammers will often attempt to further perpetuate a successful phishing email attack by sending similar emails out to the entire contact list available in your mailbox (for some people this can be hundreds or even thousands of contacts). Even worse, the new phishing emails will be coming from a trusted sender, you! Not only does this hurt you and your business’ reputation, it can increase the likelihood of one of your vendors or partners being compromised by the new wave of phishing attacks coming from your email account.
6 steps to take if you’re a victim of a phishing attack
What happens when one of your employees clicks on a phishing email and transfers a large payment for services away from your business’s bank account to a fraudulent bank account? And then what if that incident turns into a breach that exposes your entire network? Or if an employee clicks on a compromised link, and enters company passwords into a malicious website pretending to be legitimate?
If your business is victim to a phishing attack, acting quickly and following an incident response plan will help minimize potential damage. Some of the immediate steps that you could take when this occurs include:
- File a report to the authorities: If applicable, file a report to the relevant authorities, such as local police or the FBI’s Internet Crime Complaint Center(IC3)
- If a fraudulent payment or transfer has occurred, contact the bank: Notify your bank as soon as possible about the fraudulent transaction, and request assistance with stopping or recovering the payment.
- Investigate the incident: Conduct an investigation to determine what happened and how the attacker was able to gain access. This will help you identify any vulnerabilities in your systems or processes that need to be addressed.
- Get legal and financial advice: Consider seeking legal and financial advice on how to recover the lost funds.
- Notify the appropriate parties: If any sensitive information has been compromised, you may need to notify your customers or other stakeholders about the incident. This can be required by law in certain jurisdictions.
- Take steps to prevent future attacks: After the incident, work to implement additional security measures or changes to your company’s policies and procedures to prevent future attacks.
It’s important to act quickly when responding to a cybercrime incident affecting your business, but even more important to have the necessary processes and protections in place before you need to use them. Even small efforts towards better cybersecurity posture for your business can increase your company’s odds when it comes to recovering from a cyber attack.
8 steps to protect your business against cyber attacks
Peace of mind for your business’s cybersecurity doesn’t come from quick fixes or turning a blind eye to digital threats strong enough to put you out of business. It all comes down to a total risk management solution that provides peace of mind. This includes:
- Managed Endpoint Detection and Response (MDR) to provide 24/7 365 cybersecurity analyst threat hunting and monitoring
- Isolated server and file backups to prevent backup corruption or encryption by malicious actors
- Next-generation antivirus and anti-ransomware to automatically detect and block zero day threats
- Firewalls with Synchronized Security to intelligently isolate compromised endpoints from critical company servers
- Remote Monitoring and Management (RMM) software to proactively patch your systems and alert for detected issues
- Multi-factor authentication everywhere
- Cybersecurity training for employees
- Cyber insurance coverage specifically for your industry, size and risk
Investing in protecting your business against cybercrime will set your company apart from your competitors (most clients or potential clients will appreciate the effort to protect any data or services that you provide). Not to mention, you’ll still be able to keep your business open and running, while competitors who failed to properly protect their business against cybercrime won’t. The best time to have protected your business was yesterday, but the second best time is today!
Should I get cybersecurity insurance?
All of the preparation, training, and cybersecurity products in the world can’t protect you 100% of the time (although having quality preparation, training and security tools in place can greatly reduce the scope and impact of a cybercrime incident). The phishing examples listed above rely on the weakest link in the technology chain – the individual employee (also known as a Social Engineering attack). All it takes is one click!
Cybersecurity insurance can be invaluable to your company. It can cover a multitude of necessary expenses, from hiring an incident response team to quickly stop an active attack and determine the scope of a breach, to covering lost revenue or business resulting from a breach. Ensuring you have the correct coverage in place is critical to being able to keep the lights on in a worst case scenario. Making sure you have an expert to guide you to the best cybersecurity insurance policy for your own business is paramount.
How do I get cybersecurity insurance for my business?
You can check with your current insurance carrier – some offer cybersecurity insurance policy additions – but you likely won’t be dealing with an insurance agent who only deals with and completely understands all of the nuances of cybersecurity insurance coverage. This can keep you from getting the best policy for the best price, and in some cases can lead you to believing you have coverage you need when you actually don’t!
Having a trusted advisor can make all the difference when navigating the multitude of cybersecurity and cyber insurance options available. You can rely on Cyberficient to be that trusted advisor, and provide the guidance your business needs to be secure and prepared for any cybercrime incidents. We tailor our services to match the way your business operates, and partner with dedicated cybersecurity insurance specialists. Check out our Managed IT Services offering, or fill out the contact form below to ask about a free cybersecurity insurance policy review.
Contact Cyberficient to learn more about protecting your business today and tomorrow.
Here’s why business owners seek a complete risk management solution
Click here to learn more about our partner program with FifthWall Solutions.

